Forensic Chapter 6 - Smartphone Forensic
1. Comparation Between Mobile Device and PC
| iphone | Mac | |
|---|---|---|
| Computing power | = | = |
| Storage | < | a bit larger |
| Ram | = | = |
| Connectivity | > | Need a WIFI or Ethernet |
| Power consumption | < | |
| System | Advanced | |
| Security | Encrypted storage |
2. Acquisition Types
Logical Acquisition
A high-leve acquisition, normally describe the action of copying that allowed by the system.- Pros: easy and time friendly and no need to wipe the trace of this kind of actions.
- Cons: limited capabilities.
File System Acquisition
A middle-level acquisition copys the file system’s structure, including the existing logical objects lying on top of it.- Pros: Can recover deleted objects.
- Cons: long time needed, harder than logical acquisition.
Physical Acquisition
a bit-by-bit copy of the storage media.- Pros: very powerful.
- Cons: Hard, long time needed.
3. Data Extraction Types
- Manual Extraction
- Logical Extraction
- Physical Extraction
- JTAG & Chip-Off
4. Privilege Gaining Techniques
Android -> Rooting
- Permanent: replace kernel
- Temporary: forensic software, a usual restart can cause it reversing to un-rooted state
IOS -> Jailbreaking
- Tethered Jailbreaking: reset after restarting, device won’t function fully until jailbreaking again.
- Semi-tethered Jailbreaking: reset after restarting, device retains most of its function except those requires elevation or outside of normal operating parameters.
- Untethered Jailbreaking: permanent until system upgrade.
Restrictions
- secure applications like banking or finance-related use sand-box.
- device will be untrusted
5. Forensic Part
Remember
- Don’t turn off mobile device
- Isolate the device from network connection
Things to collect
- SIM-Card
- International Mobile Equipment Identity -> IMEI, the name of your mobile devices.
- Integrated Circuit Card ID -> ICCID, link to the owner
- International Mobile Subscriber Identity -> IMSI, find the background information about this sim card, like country, mobile network and subscriber number.
- PIN, PUK number, SIM applications
- Phone memory
- Contacts
- SMS, MMS
- Call list
- Multimedia stuff
- Calendar
- Geo-location
- Online accounts
- Browser’s history
- Password storage
- SIM-Card
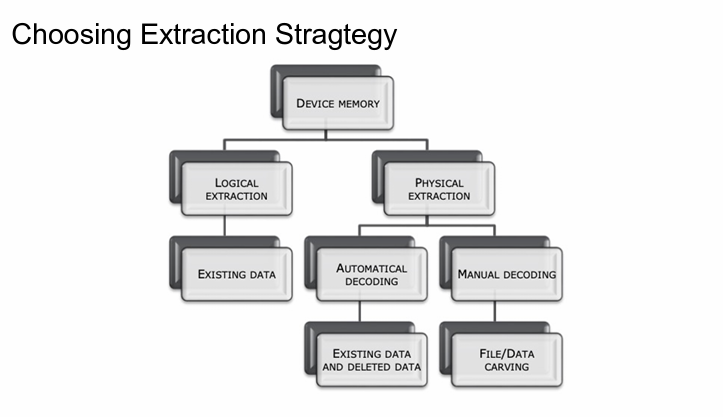
Choosing the right extraction strategy
Misc
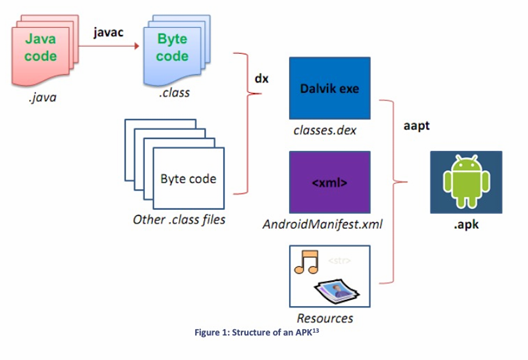
Android

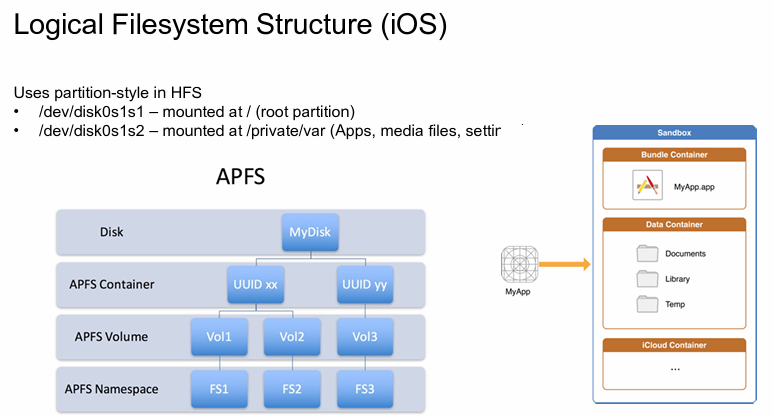
IOS
.APK
Mobile forensic tools
