Forensic Chapter 5 - Network Forensic
1. Network Layers
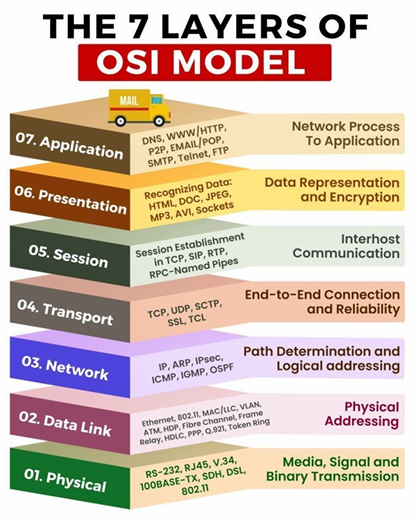
- OSI 7 layers
- TCP/IP 4 layers
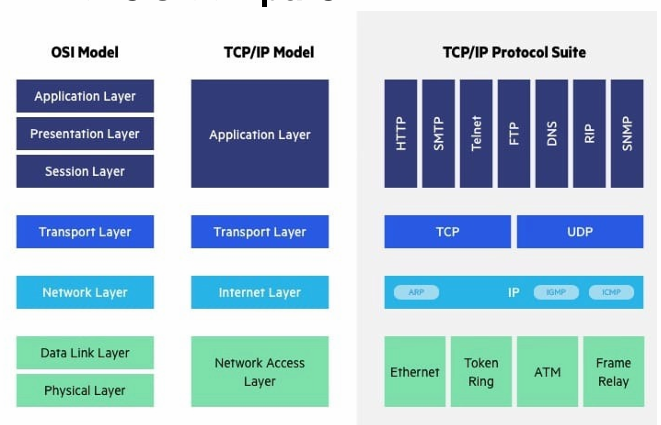
- Usually used protocols in each layer
| Application Layer | FTP, SMTP, HTTP, HTTPS, DNS, DHCP |
|---|---|
| Presentation Layer | N/A |
| Session Layer | N/A |
| Transport Layer | TCP, UDP |
| Network Layer | IP, IPSec, ICMP, IGMP, ARP |
| Data Link Layer | 802.11, MAC |
| Physical Layer | N/A |
- Differences between TCP and UDP
- TCP is a connection based protocol which means we can only communicate with one endpoint at one time (unicast).
- UDP could be used in multicast and broadcast scenaries.
- TCP is more secure than UDP because it makes sure all the messages are transmitted to the other side already.
2. Tools
- tcpdump -> a command line command used to check the stream of protocols.
- snort -> rule based network stream IDS (Intrusion detection system)
- wireshark -> GUI + tcpdump